The Harmagedon ransomware infection is a file-encrypting virus from the notorious Makop ransomware family. Windows computers infected with this cryptovirus experience data or file encryption and receive ransom demands for the decryption.
In other words, the victims of this Harmagedon ransomware virus lose access to their personal or system files and are asked to pay a ransom fee – in order to restore access to their files.
The Harmagedon virus encrypts files using a very strong cryptographic algorithm, which makes it impossible to decrypt locked files without a key and decryptor.
If you are looking for detailed information about Harmagedon ransomware infection, then you have come to the right place. In this article, you will get to know about this particular ransomware distribution methods and how you can remove the infection from your computer.
What is Harmagedon Ransomware?
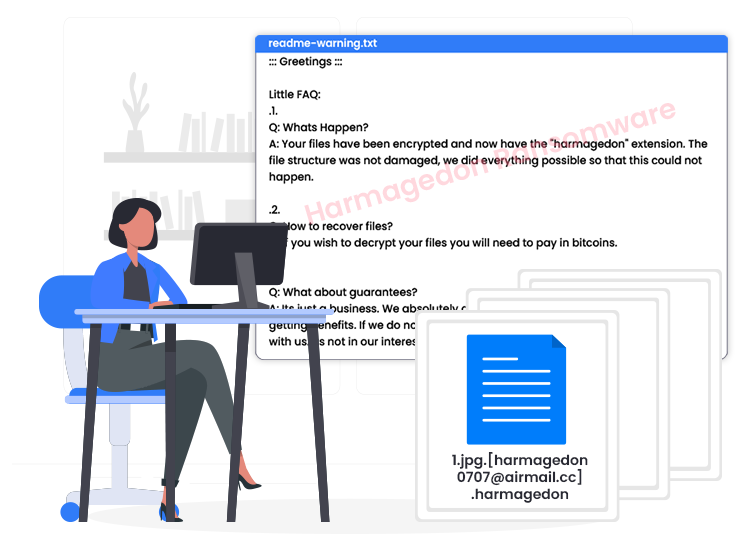
Harmagedon ransomware is a new cryptovirus or data locking malware designed by cyber crooks to encrypt users’ files stored in a system and then demand money for a decryption key. Within encryption, this data locking malware changes the name of infected files by appending the “.harmagedon” extension.
Once the encryption process is completed, the virus informs victims about the data encryption by displaying a ransom note titled “readme-warning.txt”.
How Does Harmagedon Ransomware Infect Your Computer?
Ransomware and other hazardous computer programs are designed to infect the user’s PC and get unauthorized access to the personal data stored in the hard drive. There are multiple ways through which hackers infect the device of a targeted user, some of the ways are listed below:
- Unauthorized file-hosting sites
- Unwanted software updates
- Spam emails and notifications
- Insecure download sources
- USB and other storage devices
- Pop-up advertisements and offer links
How to Remove Harmagedon Ransomware from PC?
The process of removing ransomware from a computer system can be done in two ways. First is the manual removal of the ransomware. In this, the user is required to manually search for all ways through which the virus enters a system and block them in order to protect the device. This is a very time-consuming and complex way, that’s why many users use the second way.
The next way of removing the malware and virus from the system is very common and used by many users. It requires you to use a dedicated antivirus or anti-malware software to clean all the viruses and malware infections from the device.

