Mammon ransomware is a piece of rogue software that operates by encrypting all major file types (e.g., .doc, .docx, .xls, .pdf, etc.) and demands a huge sum of ransom payment for the decryption.
Ransomware is, without a doubt, one of the fastest-growing threats to cybersecurity in today’s world. Every day, dozens of new ransomware variants are being developed and spread via the Internet. One such ransomware-type infection is Mammon.
Scroll through this article below to find out how this particular ransomware spreads and how you can completely remove it from your computer.
What is Mammon Ransomware?
Mammon is the name of a malicious program that belongs to the family of ransomware viruses. The main motive of cybercriminals behind the creation ofMammon ransomware is to extort money by fraudulent means.
Once this hazardous ransomware-type infection penetrates the targeted computers, it encrypts (locks) all the users’ files (such as office documents, images, videos) stored on the machine and then forces them to pay the attackers a hefty sum of ransom amount in the form of Bitcoin to get the decryption key/tool.
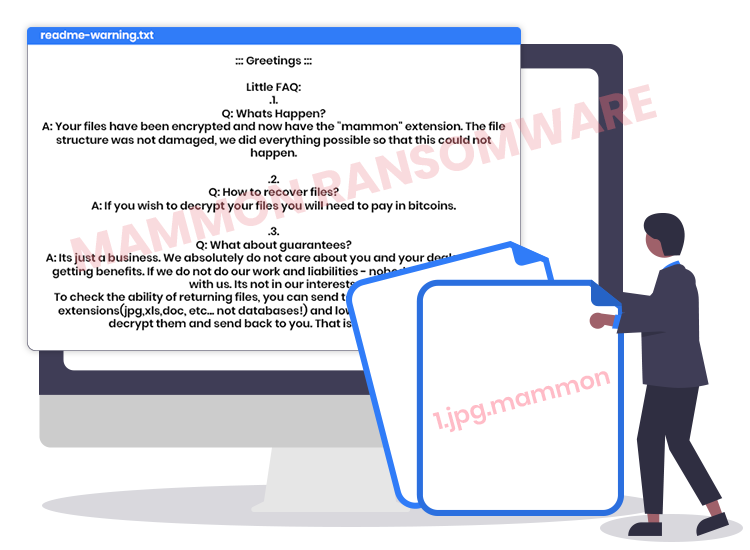
Like Combo13, Rootiunik, Kfuald, and other ransomware-type programs, it changes the name of each of the encrypted files by appending a unique extension (“.[mammon0503@tutanota.com].mammon”). For example, it renames a file originally titled “1.jpg” to “1.jpg.[mammon0503@tutanota.com].mammon”, “2.jpg” to “2.jpg.[mammon0503@tutanota.com].mammon”, and so on.
Once this encryption process gets complete, Mammon places a special text file (ransom note) named “readme-warning.txt” into every folder containing the encrypted data.
The message in the “readme-warning.txt” file informs victims that all of their files have been encrypted using military-grade cryptography algorithms. To regain data access, the note instructs victims to contact the attackers via the given email address to get detailed instructions on how to purchase a decryption key/software.
How Does Mammon Ransomware Infect Your Computer?
There are numerous methods used by cyber criminals to distribute ransomware and other malicious malware. The most common attack methods for ransomware are as follows:
- Phishing emails with malicious attachments
- Drive-by downloading
- Deceptive or malicious advertisements
- P2P (peer-to-peer) networks
- USB stick and other removable media devices
- Freeware download websites
- Free file hosting or porn sites
- Fake software updating tools
How to Remove Mammon Ransomware?
The simplest and most effective way to delete Mammon and other dangerous malware infections is to perform a full system scan using a potent antivirus or antimalware software.


1 Comment