RedDot ransomware was discovered by a malware analyst named Jirehlov Solace. Computers systems infected with this type of malware infection experience data encryption (files converted into inaccessible format) and receive a file containing ransom demanding message for the decryption key/software (access recovery).
Like MMTA, Venus, Yajoza, and several other ransomware-type programs, RedDot uses asymmetric cryptographic algorithms (RSA-2048 or RSA-4096) to encrypt all kinds of victims’ files, such as pictures, audios, videos, spreadsheets, games, archives documents, and other data on the host system.
Many Windows users are recently found reporting that they are unable to access or open their personal files after the system is infected with RedDot ransomware. So, if you happen to be one of those unlucky fellows, then keep reading this guide to learn how to remove it from your computer.
What is RedDot Ransomware?
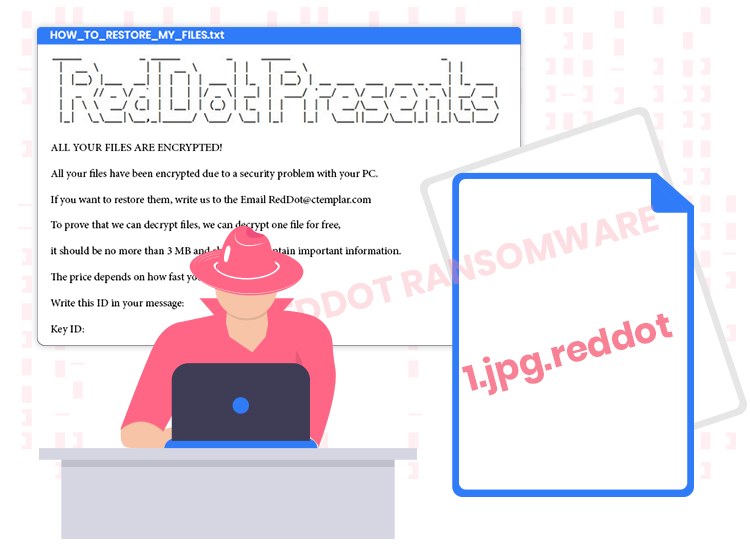
This is the name of a very dangerous file-encrypting malware that belongs to the group of ransomware viruses. Soon after the infiltration, RedDot ransomware encrypts the stored files and then renames them by adding a “.reddot” extension to the end of their original filenames. For example, it renames a file named “1.mp4” to “1.mp4.reddot”, “2.mp4” to “2.mp4.reddot”, and so on.
After encrypting the entire files stored on a victim’s computer, it generates a special text file named “HOW_TO_RESTORE_MY_FILES.txt” as its ransom note and places it in all compromised folders.
The text presented in the ransom note (“HOW_TO_RESTORE_MY_FILES.txt”) usually informs users that their images, videos, documents, and other important files have been encrypted using a very strong cryptographic algorithm. In order to recover them, they need to purchase a private decryption tool/key from the cyber crooks responsible for the ransomware infection.
How Does RedDot Ransomware Infect Your Computer?
Ransomware-type infections can be distributed to the targeted systems by potential cybercrime masterminds using various means. Here are some of the most popular ones:
- Spam emails that contain malicious or junk attachments
- Freeware software bundles
- Malicious advertisements
- Scam/ shady/ illegal web domains
- Fake software update tools
- Peer-to-Peer sharing networks
- Software vulnerabilities
How to Remove RedDot Ransomware from PC?
The safest and most convenient way to delete RedDot ransomware and other dangerous security threats is to fully scan your infected device using a potent and reliable anti-malware tool.


1 Comment